By David Edwards and John Byrne - RawStory.com
August 12, 2009
A team of computer scientists at University of California, San Diego, the University of Michigan and Princeton University announced a new way to electronically steal votes Monday.
“We wanted to find if a real criminal could do this, starting from scratch, with no access to source code or other closely guarded technical information,” the announcer begins. “We faced several challenges: getting a voting machine, figuring out how it works, discovering a weakness, overcoming the machine’s security features and constructing attack software.”
“In the end we found that it is possible to undetectably change votes and that such an attack takes a lot less time and money than one might expect,” the announcer said.
A Princeton professor was able to acquire five voting machines for just $82 that had been resold on a government surplus website. The acquired machines were originally sold by Sequoia Voting Systems.
While the voting machines were older and had been discontinued by North Carolina, where they were originally used, the voting apparatus are still in use in Louisiana and New Jersey.
Professors and computer science graduate students found that they could switch votes use a technique called “return oriented programming.”
The students theorized that voting machines could be easily broken into by attackers the night before the election, and vote hacking software installed. The following day, machines would produce altered votes without being able to be detected.
Con't
"Hello to our friends and fans in domestic surveillance."
Subscribe to:
Post Comments (Atom)

 .
.








 May love and laughter light your days,
and warm your heart and home.
May good and faithful friends be yours,
wherever you may roam.
May peace and plenty bless your world
with joy that long endures.
May all life's passing seasons
bring the best to you and yours !
*******
Thanks Pbtrue1. :)
May love and laughter light your days,
and warm your heart and home.
May good and faithful friends be yours,
wherever you may roam.
May peace and plenty bless your world
with joy that long endures.
May all life's passing seasons
bring the best to you and yours !
*******
Thanks Pbtrue1. :)
















































 .
"Hello to our friends and fans in domestic surveillance."
.
"Hello to our friends and fans in domestic surveillance."

















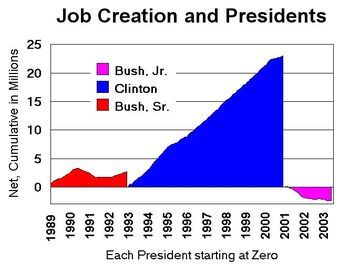












 *Hee Hee*
Submitted by Alice on Sun, 08/05/2007 - 4:02am.
MM.. :)
*Hee Hee*
Submitted by Alice on Sun, 08/05/2007 - 4:02am.
MM.. :)
 I'm Eighteen (Album Version)
I'm Eighteen (Album Version)
No comments:
Post a Comment